In the past year a lot has happened at CITL:
- We compared the utilization of application armoring techniques across thousands of applications within Windows 10, Linux Ubuntu and Linux Gentoo, and Mac OS X.
- We hacked up a proof-of-concept of our toolchain and looked under the hood at IoT applications and operating systems in use on “Smart” TVs.
- We found safety issues that seemed to have gone unnoticed for years in popular applications (e.g. Firefox and Office 2011 on OS X).
- We provided both high level and detailed results of our findings and approaches in our presentations at BlackHat and Defcon.
- We collaborated Consumer Reports and other public interest organizations to codify how to assess security risks to consumers in the products they buy.
When a new suite of a familiar piece of software comes out, you have to decide if you want to upgrade or not. Sometimes there's a long-awaited feature, and you can't wait to get the latest and greatest, and sometimes it looks an awful lot like what you've already got, so it doesn't really seem worth the bother. The security and software risk profiles of the old vs new versions are another factor that should be part of this consideration.
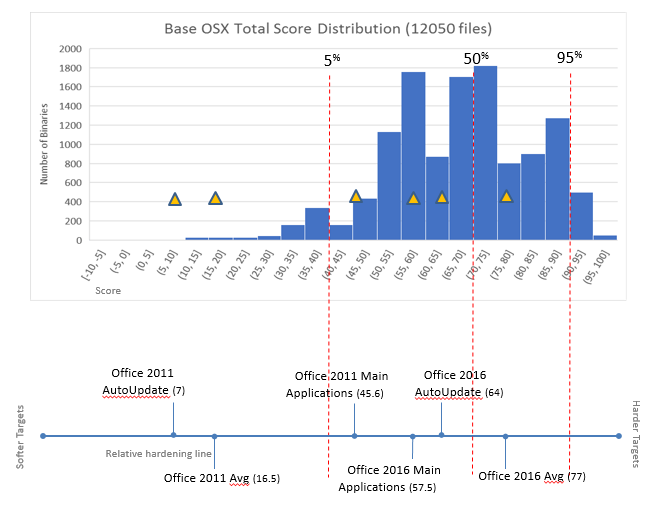
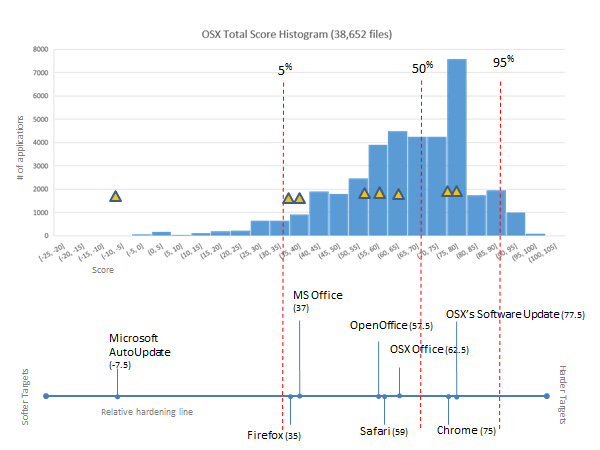
When we looked at scores for OSX applications, the Microsoft Office 2011 suite was at the bottom of its category, and the accompanying Microsoft AutoUpdate application was at the bottom of the whole OSX environment. Since then we've been asked how Office 2016 stacks up in comparison, and it provides an excellent example of hidden benefits of an upgrade, as it has a much better risk profile than the 2011 suite.
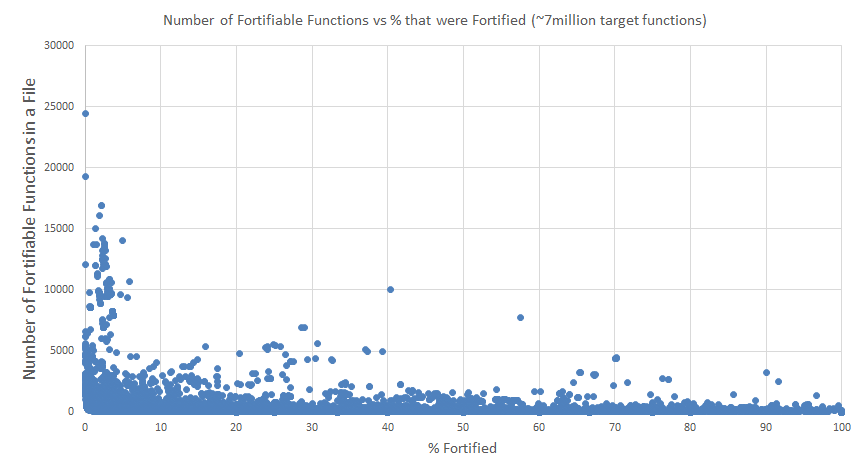
Source fortification is a powerful tool in modern compilers. When enabled, the compiler will inspect the code and attempt to automatically replace risky functions with safer, better-bounded versions. Of course, the compiler can only do that if it can figure out what those bounds should be, which isn't always easy. The developer does not get much feedback as to the success rate of this process, though. The developer knows that they may have enabled source code fortification (-D_FORTIFY_SOURCE), but they do not get a readout on how many of their memcpy instances are now replaced with the safer memcpy_chk function, for example. This is important to the consumer because just looking to see that a good software build practice was intended does not reveal whether the practice actually improved the safety in the resulting application. That made us really curious to dig into the data on source fortification and its efficacy.
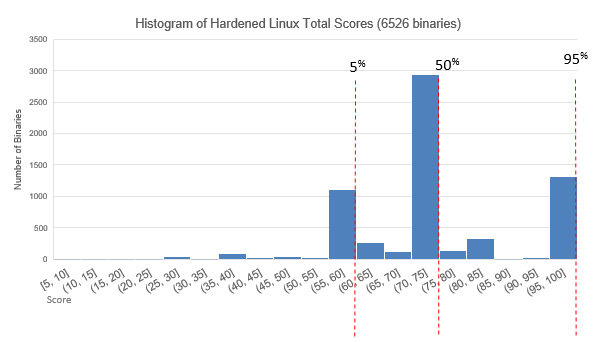
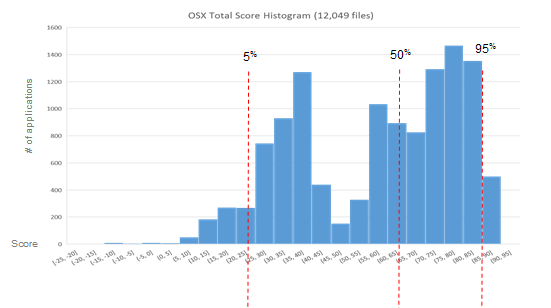
A while back, we showed what the score distributions were for base installs of three major platforms. Here, we're going to compare that base install view of Linux with the score distribution for a custom, hardened instance of Linux.
In our previous post about the score histograms for Windows, Linux, and OSX, we promised deeper dives to come. We also noted interesting things about each continuum and reminded people that the real value is being able to compare risk present in various software within a single continuum. No we will take our first look at where some applications of interest live on the score continuum for OSX. We'll look at three categories of software here: browsers, office suites, and update software.
If you've seen our post about the score distributions in OSX, Linux, and Windows 10 base installs, your first question is probably about what factors go into computing those scores. This post will provide some high level understanding of what factors we consider for those static analysis scores.
The main question we're trying to find the answer to is, "How difficult is it for an attacker to find a new exploit for this software?". Attackers have limited resources, and just like anyone else, they don't like to waste their time doing something the hard way if an easier path is available. They have tricks and heuristics they use to assess the relative difficulty to exploit software ...
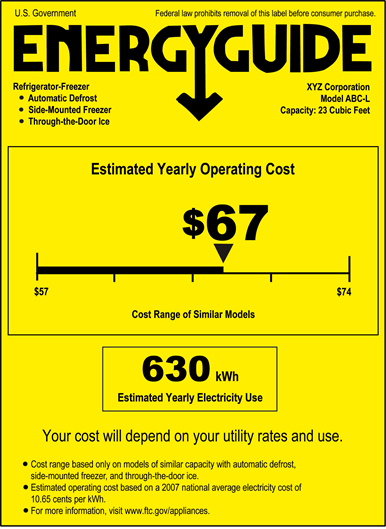
Evaluating the risk profile of software is a technically complex task, but there are lots of other industries where consumers have to engage in complex decision-making. Choosing which car is the best choice for you, or which food best fits your diet, or which new refrigerator to buy are all very technically complex decisions, but those industries have all developed (mandatory) labels to help consumers stay informed...
So, first off, thank you! We've been thrilled so far by the media coverage and security community reaction we received. It was particularly exciting to hear people in other Defcon and Black Hat talks speculating on how our efforts could be used to inform/support/feed into theirs (Thanks, Jeremiah!). While our main reports and content will be tailored to a broader audience, we definitely want our data to be a tool that the security researcher community can make use of. We also think that this detailed data will be extremely useful to the insurance industry as actuarial data to inform their cyber insurance practices....